Access AWS Config Logs With AWS SSO User
I recently noticed a sudden increase in the AWS Config cost in the production environment. Because we are using AWS Control Tower to govern and manage the company’s AWS accounts, we get out-of-the-box a dedicated AWS account where all logs are shipped to it, and part of these logs is the AWS Config logs. The name of this account is Log Archive.
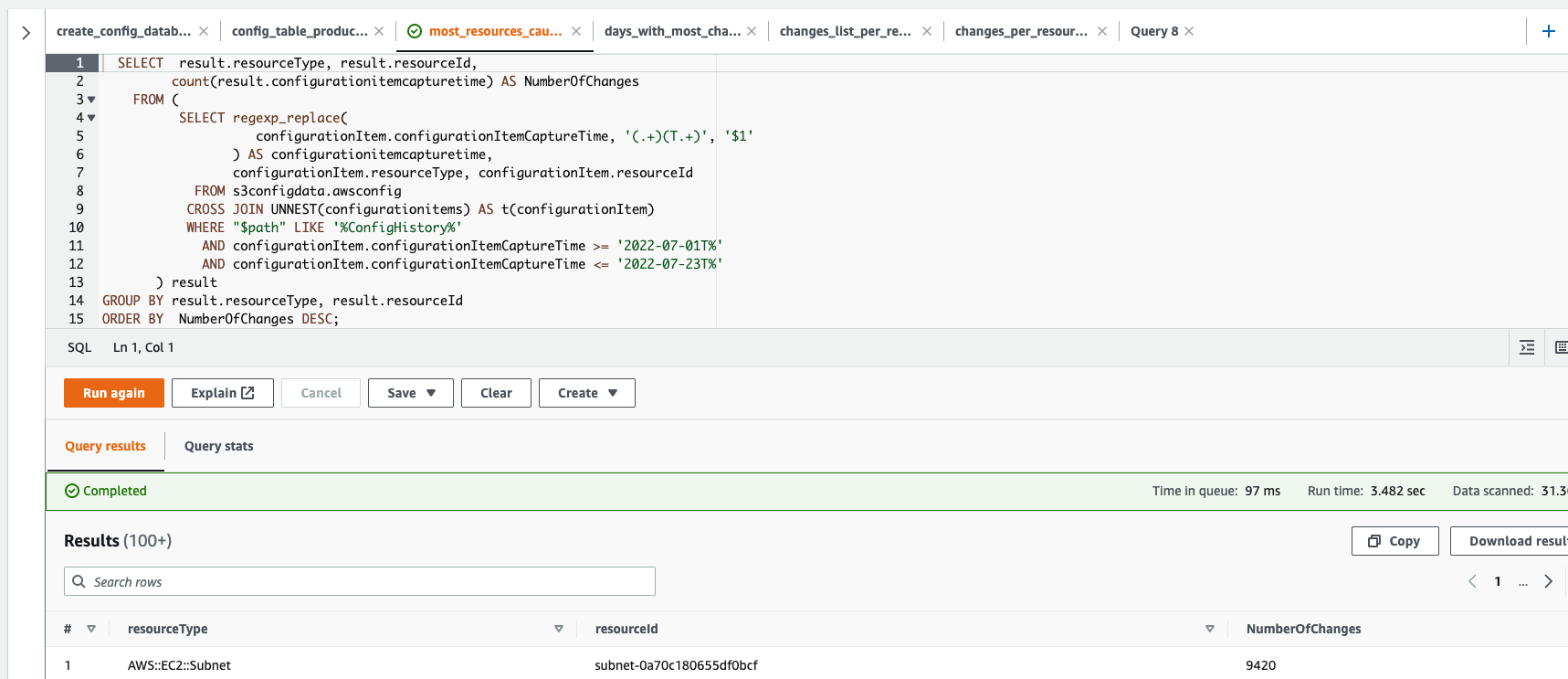
The AWS Config logs are saved as files in S3 bucket, and these files are partitioned in a way that allow Athena to query them. After setting up the Athena table and write the first query, I got an error complaining about the lack of permissions to read the S3 bucket data!
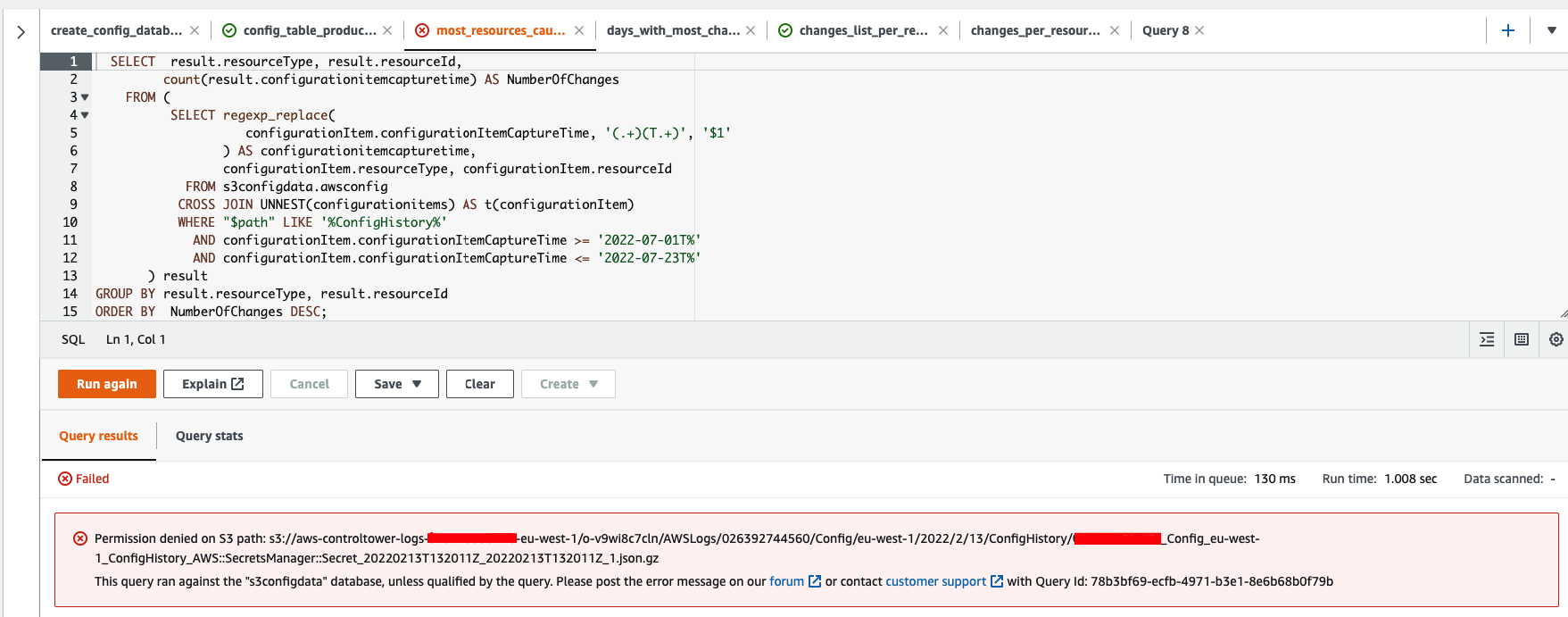
I was logged in the account using the AWSAdministratorAccess SSO Permission Set, which have administrator access to the account. I went to check the S3 bucket that have the files to see of there an explicit permission that denies access to the bucket data, but found nothing. Then I went to check one of the files saved in the bucket and tried to download it but get another access denied error!
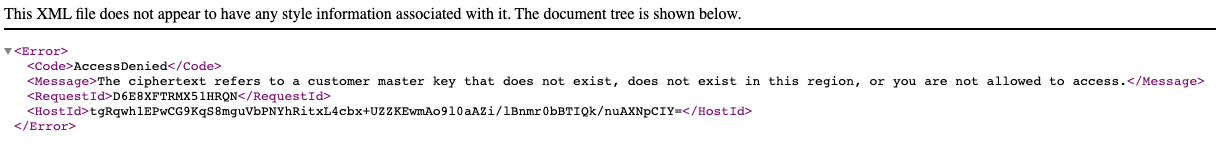
I thought that could be a file permission that prevent me from accessing the file, so I checked the permission tab, yet nothing is set to deny the access to the file.
Checking the file information and scrolling down in the page I found that Server-Side Encryption is enabled and KMS key lives in the AWS Master account.
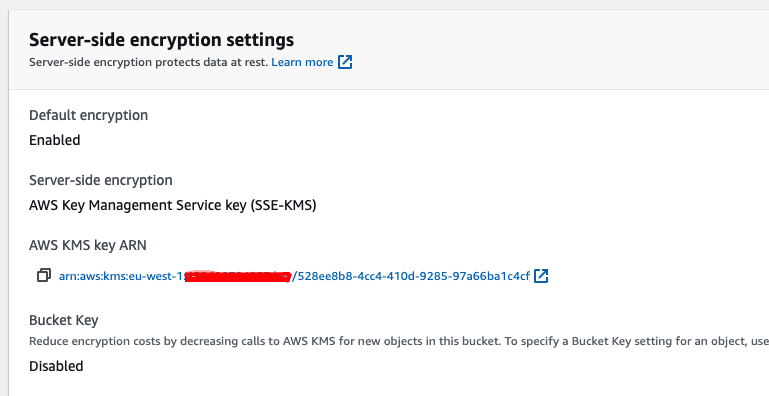
It turns out that AWS Config is configured to send the logs to S3 and encrypt them using a KMS key that is managed in the AWS Master account.
# Part of the cloudformation stack the is deployed in the all accounts managed by AWs Control Twoer.
Resources:
ConfigDeliveryChannel:
Type: AWS::Config::DeliveryChannel
Properties:
Name: !Sub ${ManagedResourcePrefix}-BaselineConfigDeliveryChannel
ConfigSnapshotDeliveryProperties:
DeliveryFrequency: !FindInMap
- Settings
- FrequencyMap
- !Ref Frequency
S3BucketName: !Ref AuditBucketName
S3KeyPrefix: !Ref AWSLogsS3KeyPrefix
SnsTopicARN: !Sub arn:aws:sns:${AWS::Region}:${SecurityAccountId}:${AllConfigTopicName}
S3KmsKeyArn: !If
- IsUsingKmsKey # is True
- !Ref KMSKeyArn # equal to Master KMS key, arn:aws:kms:eu-west-1:zzzzzzzzz:key/528ee8b8-4cc4-410d-9285-97a66ba1c4cf
- !Ref AWS::NoValue
Creating AWS SSO user with the required permissions to access the encrypted logs
When AWS Athene read the data from S3 bucket, it uses the current user IAM permissions. This means that I need to grant the user I will use permissions to decrypt the Master KMS key. Also, To do that, I’m going create new AWS SSO Permission Set, and call it AdminSecurityAudit. Then grant this group a permission to full access the account and decrypt the Master KMS key. Here are the steps:
- Login to your AWS Master account as an Administrator.
- Go AWS SSO service and start the create new permission set wizard.
- In the
Select permission set typestep chooseCustom permission set. - In the
Specify policies and permissions boundarystep:- For
AWS managed policieschooseAdministratorAccess - For
Inline policy, you need to define a policy that allowsecnryptaction for the Master KMS key
{ "Statement": [ { "Sid": "Statement1", "Effect": "Allow", "Action": [ "kms:Decrypt", "kms:DescribeKey" ], "Resource": [ "arn:aws:kms:eu-west-1:zzzzzzzzz:key/528ee8b8-4cc4-410d-9285-97a66ba1c4cf" ] } ] }- In the
Specify permission set detailsstep, fill a permission set name:AdminSecurityAudit. - Finally, review the permission set details and click the create button.
- For
- In the
- Now you need to create AWS SSO Group and add yourself to it.
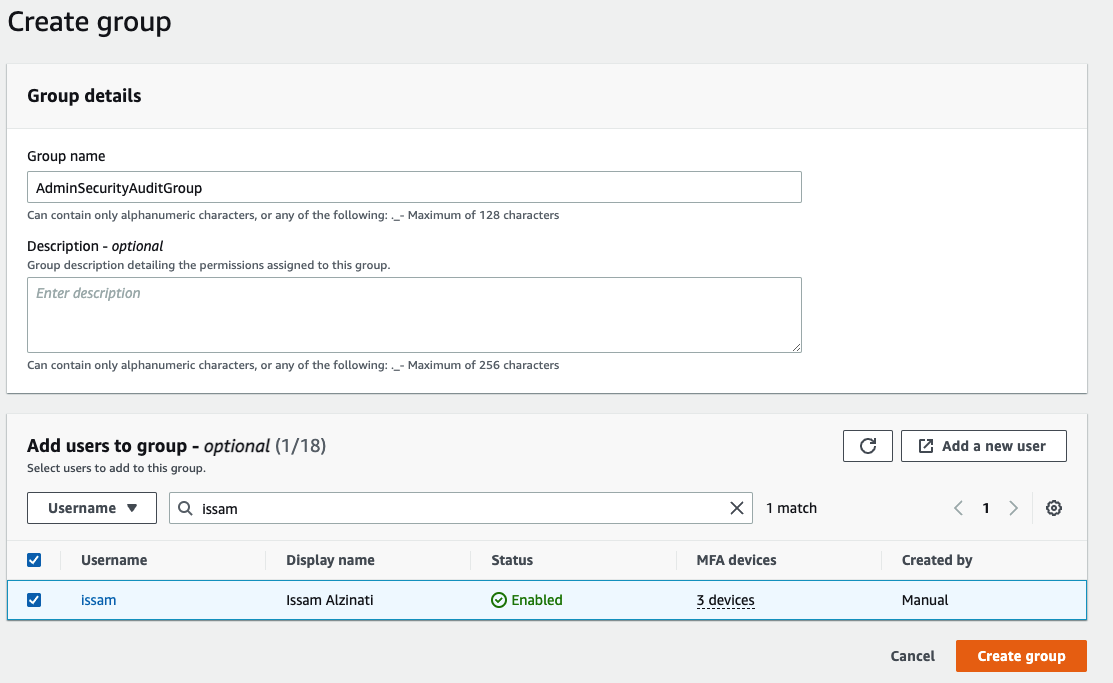
- Then you go AWS Account and choose the
Log Archiveaccount - In the
Log Archiveaccount page click onAssign users or groups
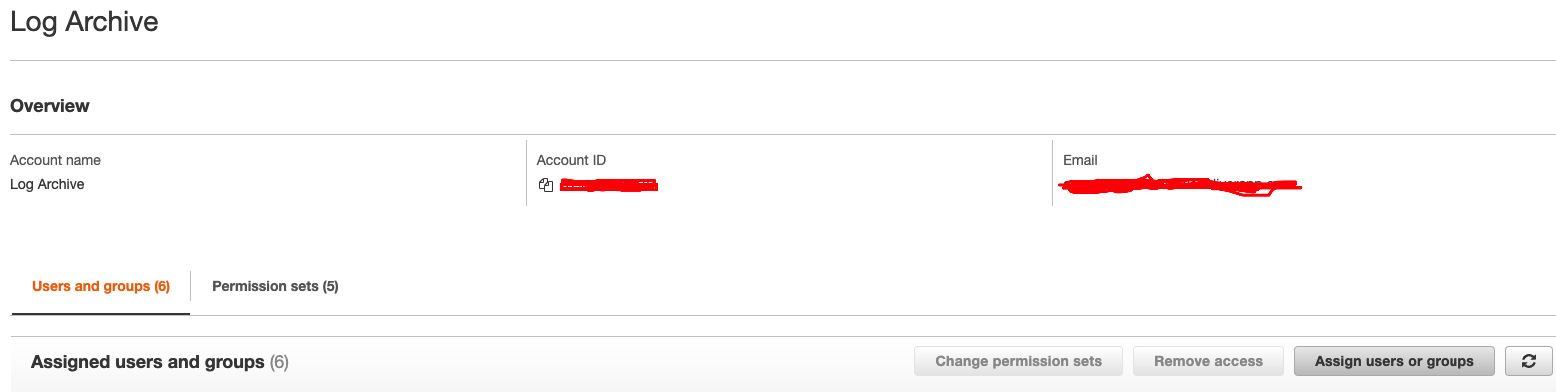
- In the
Assign users or groupsfollow the steps:- In the
Groupstab selectAdminSecurityAudit - For the permission set, search for
AdminSecurityAuditand select it. - Review and Submit.
- In the
- The new Group with the corresponding permission set will be deployed to your account.
This is not enough though to allow the user to use the Master KMS key. We need to edit the Master KMS key resource policy.
- Login to your AWS Master account as an Administrator.
- Go the KMS service page
- Click on the
managementkey. - Edit the key policy, append the following part. The AWS Principle that we need to use is the name of IAM role for the
AdminSecurityAuditpermission set we just created.
{
"Sid": "Allow SSO Admin to decrypt logs",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::xxxxxxxxxx:role/aws-reserved/sso.amazonaws.com/eu-west-1/AWSReservedSSO_AdminSecurityAudit_e73ce8da357r209c"
},
"Action": [
"kms:DescribeKey",
"kms:Decrypt"
],
"Resource": "*"
}
- Save the changes.
Now, when we log in to the Log Archive account using the permission set we just created, we will be able to run the AWS Athena queries against the encrypted log files.